One of the most fundamental issues in the field of information technology is server security, and its execution calls for a high level of expertise. Server security includes a range of topics like network security, operating system security, web services security, and their security configuration. In this article, all server security requirements—the basis of websites and online data—will be looked at and discussed. We also want to teach you how to test security of VPS server.
Table of Contents
Why cPanel VPS Hosting?
Although shared hosting may be the cheapest option, it has many issues. Since you share system resources with many other users, you need to know that the performance will be satisfactory. Sharing an IP with numerous users might have adverse effects, exceptionally if your “neighbors” choose to send spam.
A virtual private server gives you much better security and more dependable performance. You are assured of receiving dedicated hardware resources always available to you. You won’t need to be concerned about your dedicated IP becoming blocked because you will be the only one using it. The host gives you complete control over it because you are the only user on the server. If you know what you’re doing, a VPS is highly adaptable to customizations and can achieve anything.
How To Analyze a VPS Server’s Security
Shared hosting providers should pay greater attention to security because several websites are shared on a single server and utilize the same amount of storage and resources. Stay with us to learn more about this in the next section of this article. How to test security of VPS server.
Start Working With The Server
Because we are using windows as our operating system, we can communicate with Linux servers using the putty program and with windows servers using the remote desktop connection. After installing the server’s operating system and services, you should follow security-related guidelines, such as restricting and turning down useless services.
Server Security Measures
You must update security services in companies and organizations with these changes since security risks, and methods of attack in the new era have taken on a unique shape and are changing daily. The term “information security services” refers to a group of security services covering various information and server security requirements for businesses and organizations.
Examples of these threats include the spread of spyware and malware by internal and external agents and the leakage of sensitive data by these agents.
Penetration Testing

A penetration test is a procedure that analyzes the server, network, resources, and programs related to it for vulnerabilities and security gaps. Penetration testing finds vulnerabilities in the system and determines the robustness of controls.
Kinds of Penetration Testing
There are three kinds of penetration testing
- White box test
- Grey box test
- Black box test

Black Box Test
In a black box test, the tester performs the test without any prior knowledge of the system.
White Box Test
However, in the white box test, the tester has full specifications and a thorough understanding of the system, based on which he conducts a simulated attack.
Grey Box Test
In the gray box test, the tester has access to just a limited amount of information and needs more thorough knowledge.
Testing should be done based on how sensitive and secure the systems are. If high security is required, a transparent test should be run; otherwise, a gray box or black box test will do if the system and its security are not as important. Due to the risk of hardware or network system issues during the test, penetration testing should be planned and in advance coordination with the system’s owner.
Set up SIM
Using security information management (SIM) tools is one of the keys to managing an organization’s security. We can obtain exact details about a system’s activities with this program’s help so we can study them.
Software known as a security information management system gathers all system logs and responds to system logs when it notices an unexpected activity or what is known as “Bad Behavior.”
Set up IDS/IPS
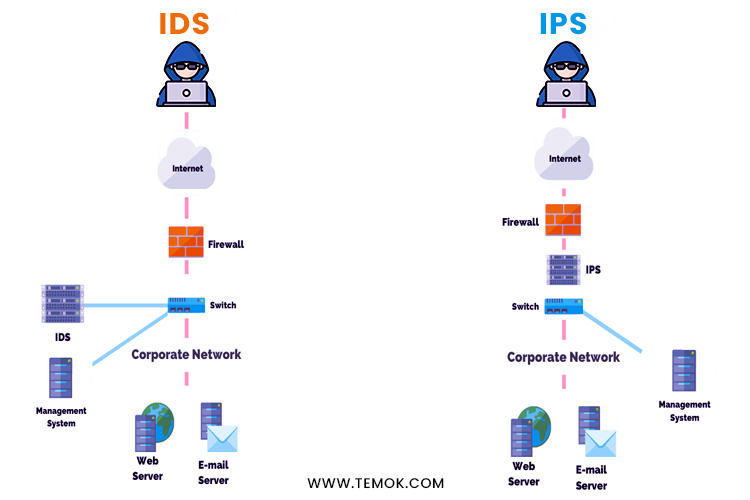
Systems have more advanced detection and prevention capabilities than firewalls for unauthorized network traffic. IDS and IPS tools monitor traffic and compare each packet with a database of known attack specifications, much like antivirus systems do.
These tools start working as soon as the attack pattern is identified. IDS and IPS have a variety of features. In actuality, an IDS is at the heart of the majority of IPSs. IDS programs identify network activity to alert malicious users about an attack, but IPS tools go one step further and automatically block harmful traffic. It is the main distinction between these technologies.
Control Security Vulnerabilities
Update management tools and security problems that help small and big networks save time, money, and bandwidth and provide security reports for connected systems and quick updates.
Security for Web Applications
Web application security testing, scanning, and patching services and products using various technologies.
Security and Risk Advice
Information security management system (ISMS) implementation and deployment is a management solution to create, implement, deploy, monitor, review, maintain, and improve information security in the organization—consulting in risk management and security of infected devices after malware attacks.
Firewall Installation

One of the security requirements of every organization is the installation of firewalls. Operating systems have software firewalls controlling incoming and outgoing traffic to the network or operating system. These firewalls are primarily used in homes, small businesses, and medium-sized organizations. Software firewalls can protect systems against unauthorized access, worms, trojan horses, and other dangerous malware.
Conclusion
Security is a major aspect of running a virtual private server, and there are many things you require to consider, especially on a self-managed VPS. To secure your server properly, you have to know the main threats, so you can create a strategy that covers as many scenarios as possible. Nowadays, every business has a web presence. But many network administrators and security managers don’t know about server security hacks. You can learn here server security hacks to secure your websites.
